Email spoofing is a deceptive practice cybercriminals use to disguise their identity by altering the sender information in emails. This manipulation makes the email appear to come from a trusted source, such as a well-known business, colleague, or friend, but it’s actually a malicious cyberattack.
The email spoofing technique is the cornerstone behind various cyber threats:
- Phishing scams
- Malware attacks
- Business email compromise (BEC) schemes
- Ransomware campaigns
- Account takeover (ATO) attacks
- Social engineering tactics
- Email bombing
Each of these attacks (and others beyond this list) exploits recipients’ inherent trust in the source of an email. They can have a profound impact on businesses and individuals.
Businesses can suffer substantial financial losses, erosion of customer trust, and long-term damage to brand reputation. Consumers may face identity theft, financial fraud, and even a breach of personal privacy.
Regardless of the victims, email spoofing is a dangerous modern-day cyber threat, but you’re not defenseless. Everything from education to cybersecurity and email authentication protocols can protect your customers and create a safer place for everyone on the internet.
Below, we’ll explain email spoofing, how it works, and best practices for preventing it.
What is email spoofing?
Email spoofing is a cyberattack technique where bad actors forge the header information of an email, making it appear as though it was sent from someone other than the actual source. This is done by manipulating fields in the email header, such as the From, Return-Path, and Reply-To addresses.
Spoofers have a range of malicious objectives, with the most common including:
- Fraud: Financial gain remains the primary motive for many spoofers. By impersonating trusted entities, they can trick victims into sending money, revealing payment information, or making unauthorized purchases.
- Phishing: Spoofing is a critical component of phishing attacks, aiming to steal sensitive information such as login credentials, social security numbers, or credit card details.
- Spreading Malware: By spoofing the identities of trusted contacts or organizations, attackers can persuade recipients to open attachments or click on links that install malware on their devices.
- BEC: In these targeted attacks, spoofers impersonate high-level executives or partners to authorize fraudulent wire transfers or obtain confidential data.
- Disinformation: Spoofing can be used to spread false information to damage reputations, manipulate stock prices, or influence public opinion.
- Espionage: Both corporate and state-sponsored actors use spoofing to gain access to trade secrets, intellectual property, or sensitive government information.
While email spoofing and phishing attacks are on the rise, they’re not a new phenomenon—the earliest instances date back to the 1970s when email and the internet were just getting started. Fortunately, today, we have more sophisticated technologies and protocols to prevent it.
Once you understand the mechanics and objectives behind email spoofing, you’ll be better prepared to defend against it. These attacks and techniques continue to evolve, which means you’ll need to stay up to date (or partner with professionals who do) to protect your business and customers.
How email spoofing works
Email spoofing tends to exploit the Simple Mail Transfer Protocol (SMTP), which is the standard communication protocol for sending emails across the internet. SMTP lacks authentication mechanisms to verify the sender’s identity, leaving room for vulnerabilities.
Spoofers forge sender information by altering the email header details that aren’t typically visible to the recipient. They manipulate fields such as the From, Reply-To, and Return-Path to display a false sender address. This is often done using malicious software or scripting that interacts with email servers to allow the spoofer to impersonate a trusted entity.
How SMTP works
SMTP was designed in the early days of the internet, and it prioritized simplicity and efficiency over security. When an email is sent, SMTP routes the message from the sender’s server to the recipient without verifying the sender’s identity.
This inherent trust is what spoofers take advantage of.
They use SMTP commands to communicate directly with email servers, instructing them to send emails with forged headers. Since SMTP doesn’t validate that the sender is who they claim to be, the email appears to come from the spoofed address.
Typical examples of email spoofing
- CEO Fraud: An employee receives an email that appears to come from the company’s CEO, asking for an urgent wire transfer to a new vendor. The email is actually from a spoofer using the CEO’s forged email address.
- Phishing: A user gets an email that seems to be from their bank, complete with official logos and branding. The email urges them to click on a link to update their account information, leading them to a fraudulent website designed to steal their credentials.
- Malware Distribution: An individual receives an email that mimics a shipping notification from a well-known courier service. The email contains an attachment that, when opened, installs malware on the user’s computer.
- Brand Impersonation: Customers of a retail company receive emails advertising a fake promotion. The emails look like they’re from the company, but they’re actually from a spoofer looking to steal personal details for identity theft.
Ways to identify and prevent email spoofing
The first step in preventing email spoofing is recognizing it. Once you know what to look for, you can better protect your business and ensure it has the protection it needs. Here are some telltale signs of a spoofed email:
- Mismatched Email Addresses: The display name might look legitimate, but the actual email address may be off by a few letters or use a suspicious domain.
- Generic Greetings: Spoofed emails often use vague salutations like “Dear Customer” instead of your name.
- Urgent or Threatening Language: Messages that push you to act quickly or threaten consequences can be a red flag.
- Unsolicited Attachments or Links: Unexpected requests to click on links or open attachments should always be treated with suspicion.
- Poor Spelling and Grammar: Professional organizations usually send well-crafted emails. Numerous errors may indicate a spoof.
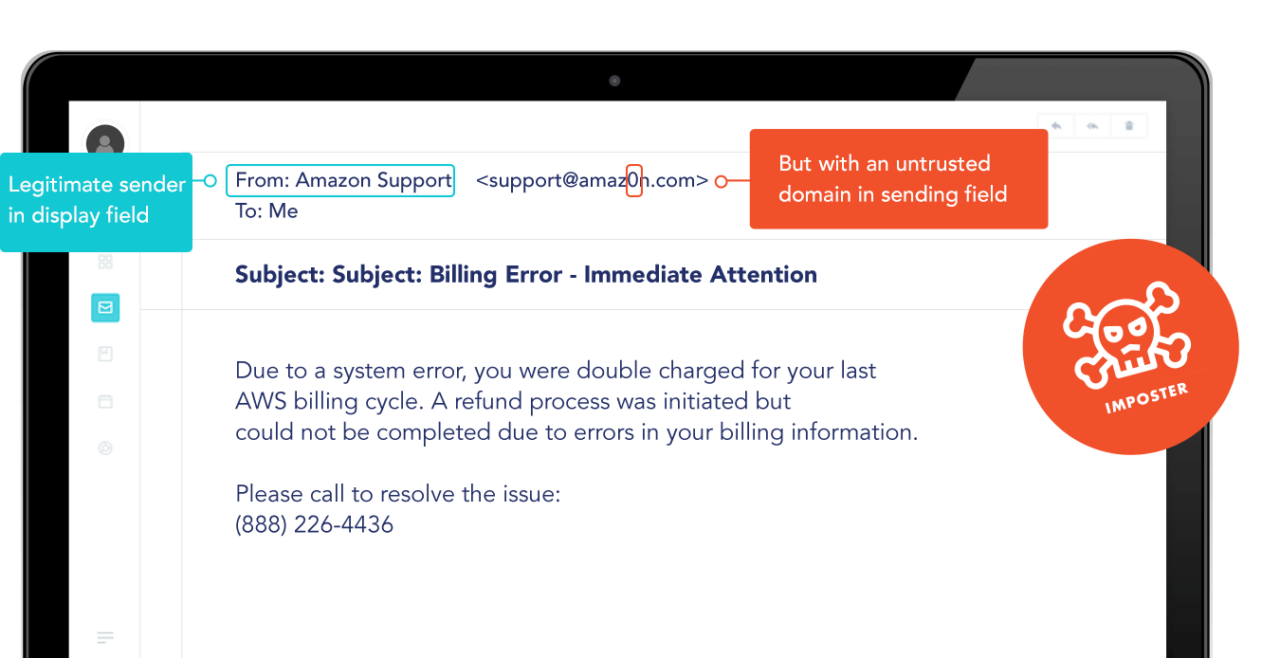
The email header contains a detailed log of the path an email has taken. By examining the header, you can often spot discrepancies indicative of spoofing. When in doubt, here are additional factors to look for:
- Check the Return-Path: This should match the sender’s email address. If it doesn’t, it’s a sign of spoofing.
- Analyze the Received Fields: These show the email’s journey. Look for any strange or unfamiliar domain names.
- Examine DKIM-Signature Field: If the email claims to be from a domain that uses DKIM but doesn’t have a valid signature, it may be spoofed.
The next step in the battle against email spoofing is prevention, and that involves stopping these emails from getting through in the first place. Here are the strategies your organization can use to adopt a multi-layered defense against email spoofing:
- Implement DMARC: Domain-based Message Authentication, Reporting, and Conformance (DMARC) helps prevent spoofers from using your domain to send unauthorized emails.
- Set up SPF Records: Sender Policy Framework (SPF) allows domain owners to specify which email servers are permitted to send email on behalf of their domain.
- Configure DKIM: DomainKeys Identified Mail (DKIM) adds a digital signature to emails, allowing the recipient to verify that the email was sent and authorized by the domain owner.
- Regularly Update Policies: Keep authentication records like SPF and DKIM up-to-date to accommodate changes in your email infrastructure.
Beyond that, you should keep your employees trained and up to date on the latest cybersecurity best practices:
- Conduct Regular Training: Educate employees about the risks of email spoofing and the importance of verifying email authenticity.
- Simulate Attacks: Use simulated phishing campaigns to teach staff how to recognize and respond to suspicious emails.
- Promote a Security-Conscious Culture: Encourage employees to report suspicious emails and make security everyone’s responsibility.
- Update Training Material: As threats evolve, so should your training. Keep materials current with the latest information on email security threats.
Work with Valimail to stop email spoofing
Email spoofing is more than a nuisance—it’s a significant security threat that can lead to data breaches, financial loss, and damaged reputations. While best practices and training provide much-needed protection, you need comprehensive email authentication solutions.
Valimail’s authentication solutions provide a seamless way to implement DMARC, SPF, and DKIM and create a holistic shield around your domain and email communications. Don’t let spoofers tarnish your brand and put your customers at risk.
Get started today by signing up for Valimail Monitor (for free) to get deep visibility into all the cloud services leveraging your domain to send email—both legitimate and BEC.