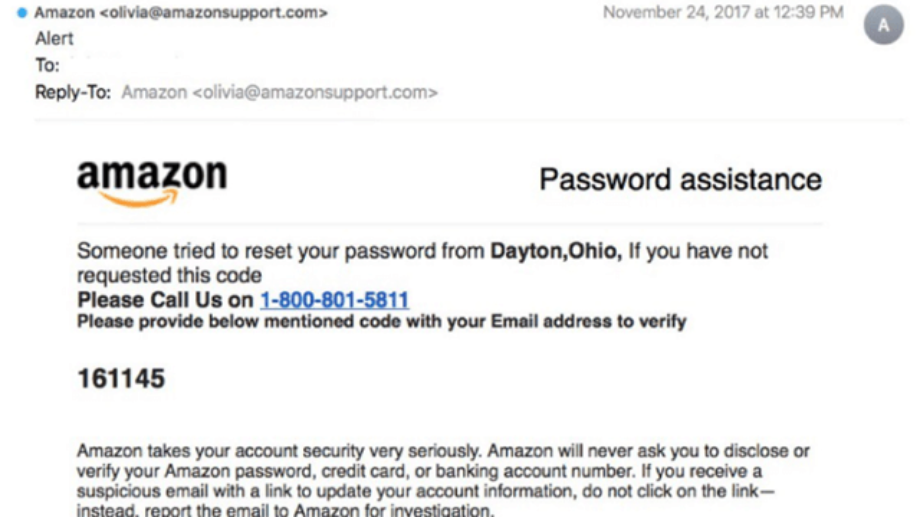
Today, we saw a phish posted by Lance Spitzner, a board member of the National Cyber Security Alliance.
This phishing email was interesting, as Lance noted, because there was no attachment and it contained no malicious links. It looked like a perfectly legitimate email from Amazon, and every domain used in the message body and its headers was a legit Amazon email. In fact, the only thing amiss with the message was the phone number, which was really a tech support scam.
This shows just how devious and hard to detect phishing emails can be. While this kind of phish doesn’t often get media coverage (possibly because it’s so rarely detected), we know that it accounts for the majority of email attacks.
1: Same-domain impersonation is ridiculously easy.
Same-domain impersonation, also known as direct spoofing or reply-to spoofing, is a type of attack in which scammers put the actual domain of the company they’re impersonating into the From fields of their phish.
It’s ridiculously easy, because without email authentication, there are absolutely no safeguards to prevent abuse of the From field. You can literally fake an email from almost anyone in about 5 minutes.
That’s why this kind of impersonation accounts for 40-60 percent of business email compromise attacks, according to Proofpoint. In another study, GreatHorn found that it accounted for 37.5 percent of all inbound email threats, more than any other category. Meanwhile, in our analysis of almost 3 billion messages sent during the month of October, 2017, Valimail found that about 1 in 5 came from an unauthorized sender — i.e., were likely fraudulent.
2: Phishing emails are undetectable by spam filters.
Spam filters operate by looking for anomalies, such as text like “VIAGRA” in all caps, which you are highly unlikely to find in any legitimate email messages.
These filters have been pretty effective at keeping Viagra ads and Nigerian princes out of our inboxes, but they don’t work well on phishing emails. In fact, they don’t work at all.
That’s because the ideal phish is almost 100% identical to a legitimate message from the company fraudsters are trying to impersonate. There’s just one tiny change: Maybe a different URL in one of the links, or maybe a different phone number. That’s it.
Anti-phishing training often tells people to look for typos or odd spellings that might give away that a phish is illegitimate. That works, if the phishers are not very skilled. Talented phishers, like the ones who created this message, can craft messages that are totally indistinguishable from the real thing.
3: Phishers use legitimate company domains to increase credibility.
As Lance noted, there are no suspicious URLs in this message. All the domains used are legitimate domains owned by Amazon. You can even verify the ownership of the amazonsupport.com domain that the message appears to come from. Yep — it’s owned by Amazon all right.
Using legitimate domains helps enhance the credibility of the message. Anyone who clicked on the links would be taken to an actual Amazon website. That’s exactly what the scammers want, in this case, because their goal is to get the recipient to call the phone number.
4: Even if you have some degree of authentication, you may still be vulnerable.
Amazonsupport.com has an SPF record configured, and it’s in order. Many companies advise you to set up SPF for your domains as a way of increasing email deliverability as well as protecting yourself against fraud.
However, SPF alone is useless for fraud protection, as you can see in this case. That’s because there’s nothing stopping a scammer from using an SPF-protected domain in the From field of their message. SPF only applies to the Return-Path header, which most people will never see.
The only way to keep scammers from using your domain in the From field is to add a DMARC record and set it to an enforcement policy (p=reject or p=quarantine).
5: It’s critical to lock down all of your domains with DMARC.
Amazon.com, the company’s main domain, is protected by both SPF and DMARC. (You can verify that with our domain checker.) Both are correctly configured and the DMARC policy is set to enforcement, so Amazon is protected from scammers trying to use their main domain in their messages.
Unfortunately, Amazon left the Amazonsupport.com domain unprotected, with no DMARC record at all.
As long as any domain owned by a company is unprotected by DMARC, it could be used by scammers in their phishing campaigns. This applies even if you’re never use a particular domain to send email. Recipients won’t know which domains are legitimate sending domains and which aren’t.
The only way to protect yourself is to lock down every domain with a DMARC policy at enforcement.