Email domain spoofing is a major threat, regardless if you’re a small business, enterprise, or mom-and-pop shop.
Flaws in email security are among the leading causes of cybersecurity incidents for many organizations. Whether it’s ransomware, business email compromise (BEC) attacks, or a spear-phishing email that leads to cyber criminals gaining access to sensitive data, email is the common denominator.
While there are many types of email attacks, unauthenticated email domains (which allow bad actors to impersonate a person or an organization) are an especially devious and difficult-to-detect vector used by many phishers. One email is all that is needed to launch a devastating and highly sophisticated cyberattack.
What is enterprise email domain spoofing?
Enterprise email domain spoofing sounds like a plot twist in a cyber-thriller, but it’s a real and persistent threat in the digital world. This cyber menace involves forging the “From” address in an email to make it appear as though it comes from a legitimate, often well-known, organization’s domain.
The goal?
To deceive the recipient into believing that the email is authentic, thereby increasing the likelihood of the email achieving its malicious objectives (be it phishing for sensitive information, spreading malware, or conducting a scam).
Imagine receiving an email that looks like it’s from your company’s IT department. It asks you to click on a link to update your password. It appears legitimate, complete with your company’s email domain and branding.
This is email domain spoofing at work.
Attackers use specialized software to manipulate email headers, disguising their true origin. Because the underlying protocols of email (SMTP – Simple Mail Transfer Protocol) lack inherent authentication mechanisms to verify the sender’s identity, spoofing can be surprisingly easy to execute.
Risks of unauthenticated enterprise email domains
Email authentication plays a pivotal role in safeguarding an organization’s digital communication. However, when enterprise email domains remain unauthenticated, they become a prime target for cybercriminals.
These vulnerabilities open the door to a range of email-based attacks, often bypassing conventional security measures and tricking recipients into believing these communications are legitimate:
- Increased Phishing Attacks: Cybercriminals can easily spoof unauthenticated domains to send phishing emails that appear to come from within the organization, targeting employees, customers, or partners. These emails can bypass traditional security gateways, as they might not contain typical phishing indicators like malicious attachments or links.
- Compromised Internal Communication: Attacks originating from seemingly legitimate internal domains can lead to the dissemination of misinformation among employees, potentially causing internal chaos or unintentional disclosure of sensitive information.
- Damaged Customer Trust: When customers receive fraudulent emails from what appears to be a trusted enterprise domain, it can severely damage their trust and confidence in the brand, leading to loss of business and tarnished reputation.
- Reduced Email Deliverability: If email service providers detect a high volume of fraudulent activity associated with a domain, they may downgrade the domain’s reputation. This can significantly impact the deliverability of legitimate emails, potentially leading to critical communications being blocked or filtered into spam folders.
- Legal and Compliance Risks: Falling victim to spoofing attacks due to unauthenticated domains can lead to regulatory non-compliance, especially in industries governed by strict data protection and privacy regulations. This could result in hefty fines and legal challenges.
- Financial Losses: Successful phishing attacks can lead to direct financial losses through fraudulent transactions or by compromising financial information of the organization or its customers.
- Brand Reputation Damage: Frequent spoofing attacks can have a devastating long-term impact on an organization’s reputation. Restoring customer confidence and brand image after such incidents is challenging and resource-intensive.
How DMARC solves these issues
If you’re reading along and wondering what you can do to secure your email domain, the answer is simple—implement email authentication with Domain-based Message Authentication, Reporting and Conformance (DMARC).
Your organization may have already implemented Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM), two email authentication methods that DMARC builds upon. DMARC relies on and extends the benefits of SPF and DKIM and can eliminate exact-domain phishing and prevent brand and executive impersonation attacks.
A key benefit of DMARC is that it allows domain owners to specify a policy for how they’d like receivers to handle email messages that fail authentication. The enforcement policy allows domain owners to tell email receivers to put unauthenticated messages in the spam folder or reject them entirely, effectively blocking impersonators.
When a DMARC record is set to a policy of reject or quarantine — what we refer to as being at enforcement — it is the most efficient and effective deterrent of impersonation-based attacks. Enforcement is critical: Having a DMARC record without enforcement is like putting a bouncer at the front door who checks everyone’s ID — but then lets everyone in regardless of whether they’re on the guest list or not.

Reach enforcement quickly with Valimail
While DMARC implementation is a critical security measure, there are some significant pitfalls many companies face on their journey to DMARC enforcement. Trying to configure DMARC, SPF, and DKIM is time-consuming, frustrating, and difficult to do manually. That’s why it typically takes months or even years for most organizations.
Valimail offers a simple and easy-to-manage process to get your domain to DMARC enforcement and to do so quickly.
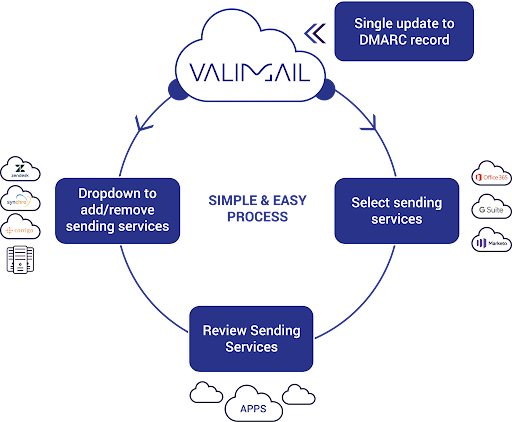
- First, you do a single DNS update to point your DMARC record to the Valimail Cloud.
- In Valimail’s interactive interface, email sending services are listed by name, not IP address, simplifying identification, and management. We make this identification more completely and more accurately than any other provider in the market. You can easily select the sending services that you want to allow to send as your domain. If you decide to add or remove a sending service or change a vendor, click the drop-down menu, and make the change.
- Once you’ve allow-listed all the senders that should be able to use your domain, you’re ready to move to enforcement. Again, with Valimail’s point-and-click interface, this is a simple selection — no DNS updates are required.
Valimail will leverage any work you’ve already done on DMARC enforcement so that you won’t have to start all over again. Unlike other solutions, 95% of Valimail’s customers achieve highly accurate and continuous DMARC enforcement with a median time to enforcement of 45 days.
An in-house IT professional typically spends less than 20% of their time getting to DMARC enforcement with Valimail. Once there, that time drops to almost zero.
Ready to start on a winning path toward DMARC enforcement?