Newly shared data from Google explains why email authentication matters and how the protocols and policies of SPF, DKIM, and DMARC are actively helping ensure a safer and more secure email ecosystem.
First, came the new requirements
Back in October 2023, Google and Yahoo announced new sender requirements that focused on (among other things) email authentication. Anyone sending significant quantities of bulk email messages to Gmail or Yahoo Mail subscribers were faced with a new compliance checklist that included Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting and Conformance (DMARC).
These new requirements help to make email more secure and safe. As Google said at the time, “Many bulk senders don’t appropriately secure and configure their systems, allowing attackers to easily hide in their midst. To help fix that, we’ve focused on a crucial aspect of email security: the validation that a sender is who they claim to be.”
From a security perspective, it makes complete sense. However, some in the worlds of email marketing and security found the requirements new and confusing. Not everybody knew about SPF, DKIM, and DMARC or why it was necessary to comply.
What followed was a period of training and education, during which Valimail, mailbox providers, email service providers (ESPs), marketing automation platforms, and many others in the industry helped to guide email senders on how to properly implement email authentication protocols and email security policy.
Next, came the deadline
With implementation deadlines looming (“enforcement beginning in February” or “sometime in Q1,” depending on whom you ask), there was a rapid rise—some might even say a mad dash—of email authentication and DMARC policy records being implemented for domains that previously lacked these settings.
In the first sixty days of 2024, we observed 2.5 million domains – more than half a million of them in the top ten million domains – newly implementing email authentication and/or DMARC policy records in DNS.
And now, thanks to Google, comes the data
This week, to coincide with a meeting of the Messaging, Malware, and Mobile Anti-Abuse Working Group (M3AAWG), Google publicized some very interesting data on email authentication and security efforts. Davey Winder, writing for Forbes, passes along this detail from Google.
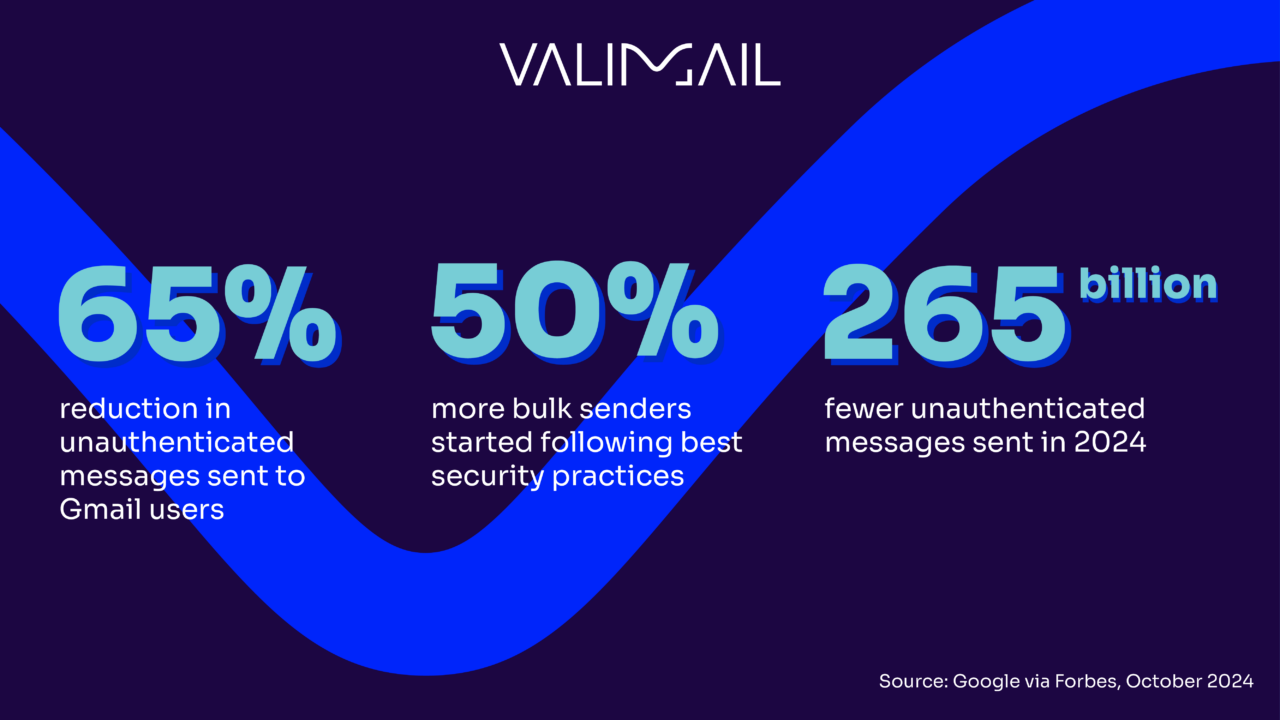
Thanks to the new sender requirements, Google has seen:
- 65% reduction in unauthenticated messages sent to Gmail users
- 50% more bulk senders started following best security practices
- 265 billion fewer unauthenticated messages sent in 2024
What does this tell us?
Google and Yahoo are clearly making an enormous impact, helping to make email more secure and helping to better protect us all against email threats.
We’re not surprised. Our industry data snapshots tell us how many domains implemented DMARC in 2024 compared to the previous year—clearly driven by the new Yahoo and Google requirements—and our own client data gives us a strong idea of how many authentication-failing email messages (across all of our clients’ domains) we help our clients prevent from being delivered.
Google is able to provide a unique view of the rest of that email universe – when it comes to domains without email authentication or DMARC protections in place, inbox providers are in a unique position to identify everything that attempts to come in through the front door. They’re the final step in the email delivery process, the gateway to the inbox. They can tell us exactly how many messages they’re rejecting or allowing through.
Google is seeing a much higher percentage of authenticated mail in 2024, with a very significant increase in email senders following email authentication and security best practices. With more email messages authenticated and more domains secure, it leads to more and better protection for Gmail’s 2.5 billion users.
Where do we go from here?
While this data is positive, it also highlights that we’ve got a long way to go. While DMARC adoption has grown significantly in the email ecosystem, there are gaps that need to be addressed.
- Most email marketers, in a rush to comply with the exact letter of the updated Google and Yahoo requirements (and nothing beyond), implemented a DMARC record with no reporting (RUA) mechanism in place. Reporting is vital for compliance: it tells you if something goes wrong with email authentication settings or if somebody is spoofing your domain name. Without reporting, you’re blind to this and other issues.
- Along those same lines, most email marketers implemented a DMARC policy of p=none. Remember that bad guys actively look for domains with a DMARC policy of p=none because, in this unprotected state, domains are vulnerable to phishing and spoofing. A DMARC policy of p=none is a starting point for a DMARC journey and not a suitable destination.
- Even with so many people coming to learn about DMARC thanks to Yahoo and Google’s efforts, many more email senders have yet to learn about email authentication and domain protection best practices.
And don’t be complacent—just because you set up DMARC one time ago, early in 2024, doesn’t mean that everything is current or up to date. You should periodically review settings, reports, and configuration.
Be prepared to implement additional configuration changes and comply with newly updated requirements in the future. Because these requirements will evolve over time, we expect Google and Yahoo to tighten up requirements further in the near future.
It’s time to get compliant
Don’t leave your domain’s security to chance—take proactive steps to protect your brand today. Sign up for Valimail Monitor (it’s free) to identify all services and sending activity from your domains. It’s the perfect first step to securing your domain.
Industry Research and Community Engagement Lead at Valimail
Al Iverson