Back in mid-May, Estonian security researchers brought new exposure to a long-extant vulnerability in DomainKeys Identified Mail (DKIM)—how the l=tag can result in messages not being fully protected against content modification and how it could be used in DKIM replay message attacks. This vulnerability allows bad guys to send new content using an affected domain’s email digital signature, affecting that domain’s reputation in a very bad way.
What is the DKIM l=tag vulnerability?
You can find our initial review and summary of the vulnerability, as well as my previous breakdown of email sender and deliverability concerns.
TLDR? A setting in DKIM limits how many characters of an email message body are covered by a DKIM signature. Bad guys can modify content past that point in the message, re-inject it via SMTP, and have it still pass DKIM authentication checks with the bad content included.
Especially concerning is that a few email platforms and domains were observed to be using an l=tag setting of zero or one, effectively protecting no body content (or only the first character of the body. In particular, at least one email service provider platform signed messages this way.
Jump ahead to now: Current status
We (and several other good folks in the email ecosystem) have made a point of attempting to identify sending domains and marketing automation platforms to warn them that their messages aren’t secure, helping them understand exactly what that means, and nudging them to reconfigure their email servers (or nudge their sending platform to reconfigure things) to address the vulnerability. This has had some success! Multiple senders/platforms, including at least one very large email marketing automation platform, have reconfigured their systems so they are no longer affected by this vulnerability.
These efforts are ongoing; we (and others) continue to notify affected senders and offer our knowledge and assistance.
By the numbers: What the data says
I manage a spam trap feed that receives over a million messages a month (which is either quite a large number or a rather small number, depending on whom you ask). In early June, I started tracking messages in the feed showing the DKIM l=tag vulnerability. (These aren’t all spammers; spam trap feeds often catch lots of email from marketers for various reasons, including typoed addresses at signup.)
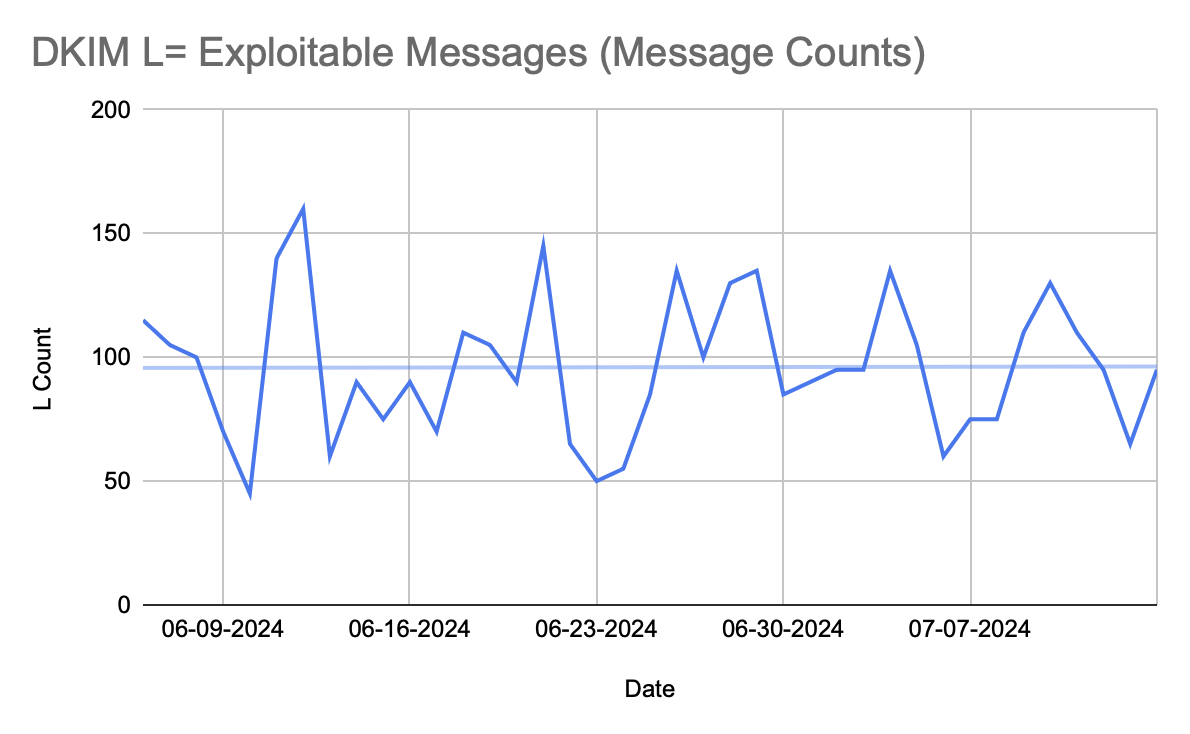
The data since early June shows that while my overall spam trap email message traffic is trending down slightly (not pictured), the raw message count of l=tag affected messages has remained about flat throughout this time. We know that we’ve helped some sending platforms address this issue, but clearly, there are enough other platforms and email domains out there configured to send in a way that leaves them exploitable via this vulnerability.
Don’t consider this issue resolved just yet
A few inbox providers have indicated that they’ll treat any DKIM-signed messages containing an l=tag as if they were unsigned, and this is very much a good thing—the lack of DKIM benefit will hopefully bubble up and be noticed by any potentially affected sender.
However, not all large inbox providers have decided to take action yet. That means there’s a good chance we’ll see a successful exploit of this vulnerability at some point, as there’s still a big enough inbox and sender universe out there to potentially make this attractive to bad actors.
Let us help secure your email
Do you need help monitoring for issues like this, identifying when messages fail authentication, identifying good and bad send sources and locales, and ensuring everything is in place to lock down your domains and move to an enforcement-focused DMARC policy?
Industry Research and Community Engagement Lead at Valimail
Al Iverson


