Valimail Enforce Enterprise customers will notice a recently launched feature: the DKIM Continuous Protection report.
This simple but powerful report and dashboard give you a single place to view everything related to the DKIM email authentication key configuration across your entire library of domain names and edit or delete key information as needed. Let’s explore what this means for you.
What is the DKIM continuous protection report?
This combination of new and updated features makes complying with DomainKeys Identified Mail (DKIM) email authentication best practices easier. Now, you can easily know when it’s time to rotate out a legacy DKIM key, retire a DKIM key due to lack of usage, and be sure that the key length complies with industry-standard best practices.
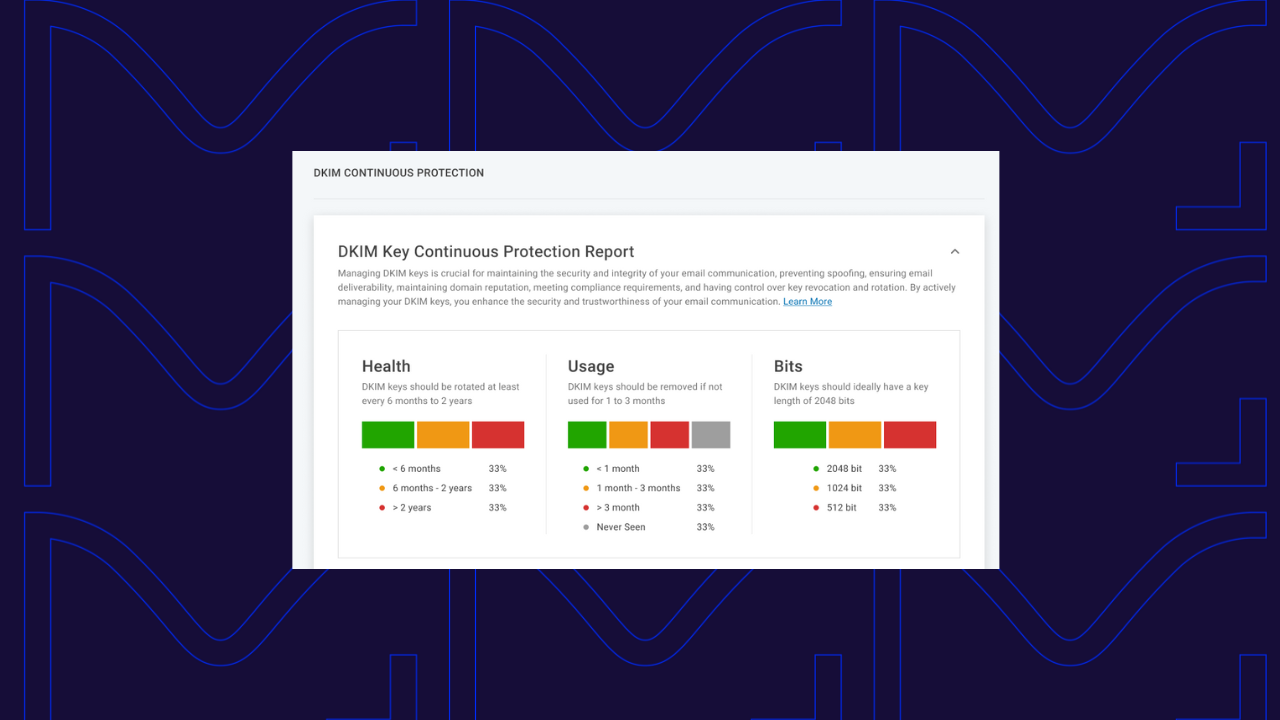
Our updated summary information display along the top of the report will help you understand the age of your currently deployed email authentication keys, whether they be less than six months old, between six months and two years old, or have been more than two years since a given DKIM key was implemented.
You’ll also be able to tell when the last time all of your DKIM keys were queried by a mailbox provider, which can help you understand whether it is now safe to delete a key after replacing it with a new one.
We’ll also help you be alert to substandard keys by showing the bit length of all implemented DKIM keys, allowing you to highlight any less than the industry standard 2048 bits.
DKIM key best practices
DKIM key best practices help you stay one step ahead of bad guys who would love to be able to sending phishing and spoofing emails with your email domain in the from address, especially if those emails could pass email authentication checks and thus pass DMARC compliance checks.
Key rotation is a very important part of this process. The longer you leave a legacy DKIM key in use, the longer an opportunity a bad guy might have to try to brute-force decrypt that key, allowing them to successfully (and scarily) spoof you in email messages. Email industry anti-abuse group M3AAWG recommends that administrators rotate their DKIM keys every six months. Leaving deprecated public keys in DNS forever can leave an email domain open to exploit via a “DKIM replay attack,” where an already existing message could be re-injected to an inbox provider and pass authentication checks just as when it was originally sent. Removing deprecated public keys in DNS could help prevent that message from unexpectedly passing email authentication checks long after its initial sending.
Key length matters, as well. Ars Technica recently reported that in 2024, it takes only $70 and 24 hours to crack a 512-bit RSA key. Those longer keys, like 1024-bit or preferably 2048-bit, are strongly recommended. At current computing standards, it might take somewhere around 300 trillion years to crack a 2048-bit key. That might be why 2048-bit is “strongly recommended” by Google and so many others.
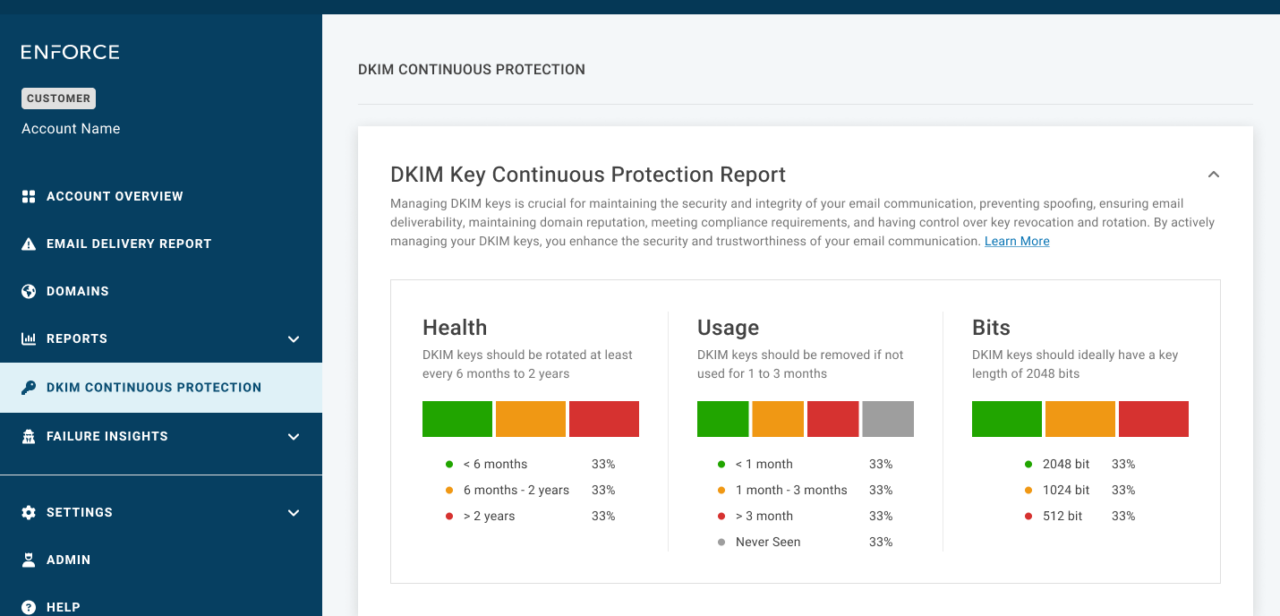
Detailed domain-level information
You’ll be able to scroll through the report and see entries for every one of your email domain names. For each domain name entry, we’ll show you:
- The Sending Platform
- The DKIM Selector
- Key Length (in Bits)
- Uploaded Date (Implementation Date)
- Last Seen Date (Last Time Queried in DNS), and
- Type (Manual or CNAME, meaning how was the DKIM key configured in our system)
We’ll also include helpful indicators to warn you if we think it has been too long since a given domain’s particular DKIM key was implemented (meaning it’s time to rotate that key out and replace it with a new one) or if a key leftover in DNS hasn’t been queried in so long that it’s safe to delete it from our system or from DNS. We’ll also warn you if the DKIM key length isn’t large enough to be considered safely secure in the long term.
Want to edit or delete any DKIM key listed? Click on the appropriate “edit” or “delete” button to the far right of a given domain name’s entry on the list.
Learn more about Valimail’s DKIM continuous protection
If you’re not already a Valimail Enforce user and would like to learn more about our automated DKIM monitoring and the other great features that allow you to protect your enterprise at scale against phishing and spoofing attacks, contact us today!
If you aren’t already a customer, you can also schedule a demo to learn about our patented and automated tech.