BETA TOOLING 🧪
Uncover malicious lookalike domains with Valimail’s free tool
For every 1 legitimate brand, there are an average of 200 malicious lookalike domains.
Phishing attacks, spoofed emails, and domain impersonation often begin with a subtle deception: a fake domain that looks just enough like yours to fool the untrained eye. These lookalike domains can erode brand trust, expose sensitive data, and open the door to inbox-based attacks.
With Valimail’s free Domain Lookalike Finder, you can instantly scan the internet for domains that closely resemble yours. Uncover typosquatting attempts, email impersonation risks, and spoofing threats before they impact your organization and take action to shut them down.
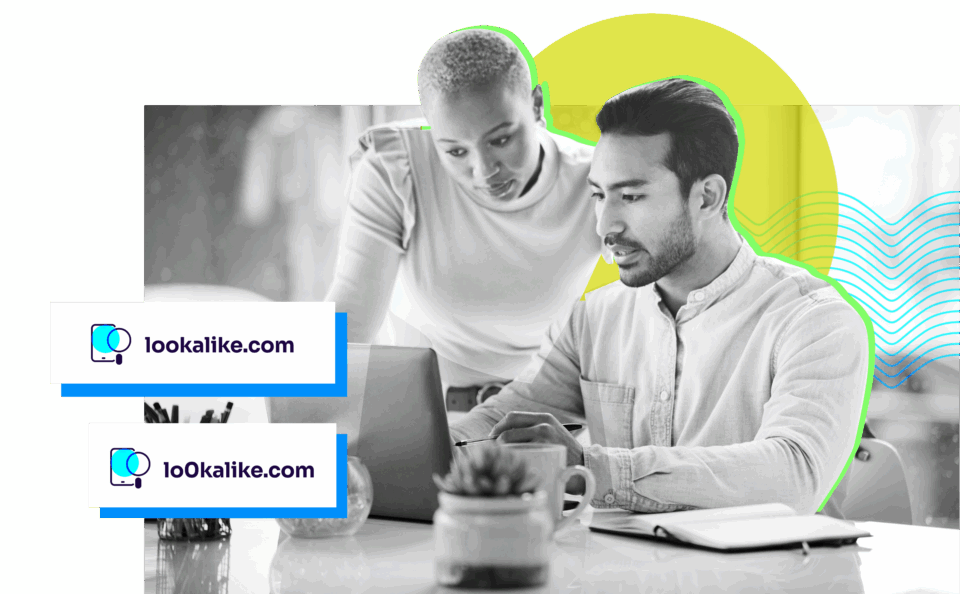
Stop your lookalike domains with Valimail
Finding lookalike domains is just the start.
To truly defend your brand, you need visibility into who’s sending on your behalf and whether they’re authorized to do so.
With Valimail Monitor, you’ll get actionable insights into your domain’s sending services, so you can spot abuse, close gaps, and prepare for DMARC enforcement with confidence.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
Learn more about defending your domain
Spotting lookalike domains is just the beginning. To build a resilient email security strategy, you need to go further by implementing authentication protocols like DMARC, understanding the tactics behind spoofing and impersonation, and actively monitoring unauthorized senders targeting your domain. Explore the resources below to strengthen your defenses, protect your brand reputation, and stay one step ahead of email-based threats.
Frequently asked questions about lookalike domains
What is a lookalike domain?
A lookalike domain is an email address that closely mimics your legitimate domain name. Lookalike domains typically have subtle misspellings or visual changes, and they’re commonly used in phishing attacks and other malicious activities to deceive recipients.
Lookalike domains use strategies such as:
- Misspellings
- Homoglyphs
- Extra characters or hyphens
- Different top-level domains (TLDs)
- Swapping letters
- Subdomains
Here’s what a lookalike domain may look like in practice:
Homoglyph attack
legitportal.com
legitp0rtal.com ← (uses “0” instead of “o”)
Swapping letters
trustpoint.com
trvstpoint.com ← (swaps “u” for “v”)
Subdomains
example-site.com
login.example-site.com ← (Appears legitimate but could be hosted on a malicious root domain)
How do lookalike domains work?

These illegitimate domains exploit human error and visual similarity, making them powerful tools for email impersonation, brand abuse, and credential theft.
What can I do about lookalike domains to protect my brand?
Protecting your brand from a fake domain name requires a mix of proactive defense, employee education, and email authentication.
Here are some actionable steps to take:
- Monitor and register similar domains.
When you’re registering your domain, also purchase high-risk lookalike domains to prevent bad actors from using them against you. Look for a similar domain with misspellings, common typos, and different TLDs.
- Use a lookalike domain monitoring tool.
If you couldn’t buy some similar domains or want to know which domains to buy, use free tools like the Valimail Lookalike Domain Finder to detect suspicious domains that closely mimic yours.
- Educate your employees and customers.
While this isn’t foolproof, training and educating can help your customers and employees spot suspicious domains and verify email sources. Awareness around these lookalike domains can reduce the risk of phishing and business email compromise (BEC)</a
- Use Multi-Factor Authentication (2FA).
Require 2FA for internal systems and key services to protect against credential theft, even if a fraudulent domain tricks users.
- Report malicious domains.
If you identify a doppleganger domain used for fraud, report it to hosting providers, registrars, and services like Google Safe Browsing or Microsoft SmartScreen for takedown.
- Enable email authentication.
Deploy DMARC with enforcement with a solution like Valimail Enforce to stop unauthorized senders from spoofing your domain. Once you’ve purchased or reported the lookalike domain, you can add it to Valimail’s platform to label it as an unauthorized sender. It’s your best line of defense against email impersonation via lookalikes.
What’s the difference between a spoofed domain and a lookalike?

A spoofed domain forges the email sender address to make it appear as though it’s coming from a legitimate domain, without actually owning or registering that domain.
On the other hand, a lookalike domain is a registered domain that visually resembles a trusted one. It is often used to trick users into clicking on malicious links or entering credentials.
Here’s a comparison:
Spoofed domain | Lookalike domain | |
|---|---|---|
Definition | A fake sender identity that pretends to come from a real domain | A domain that is registered to resemble a real one |
Control of domain | The attacker does not own the real domain | The attacker does own the fake (similar-looking) domain |
Common use case | Phishing emails claiming to be from a legitimate company | Fake login pages, phishing sites, or malicious email from lookalike domains |
Technical mechanism | Email header spoofing without DMARC enforcement | Domain registration with typos, swapped characters, or alternate TLDs |
Example | From: ceo@yourcompany.com (spoofed) | From: ceo@yourcornpany.com (registered lookalike) |
Defense strategy | DMARC enforcement to block spoofed messages | Lookalike detection tools and domain monitoring |
Why are lookalike domains so effective in phishing and spoofing?
Lookalike domains are effective because they exploit human error and visual deception. When people quickly scan an email or website, they often focus on familiar brand names or logos, not the exact characters in the domain.
Attackers take advantage of this by registering domains that are nearly identical to trusted ones, often changing just a single letter or using visually similar characters (e.g., using “rn” instead of “m” or swapping “l” with “1”).
Because these changes are so subtle, recipients may not notice anything is wrong, especially on mobile devices or in high-pressure situations like wire transfer requests or password resets.
If users aren’t trained to look closely or protections like DMARC and domain monitoring aren’t in place, they can easily fall victim without realizing it until it’s too late.
How do attackers use similar domains in phishing attacks?
Brandjacking and using a similar domain is a common phishing attack, but here’s how they’re successful:
- Fake email sender addresses
Attackers send emails from addresses like support@yourcornpany.com instead of yourcompany.com. At a glance, the difference is easy to miss, especially on mobile devices. - Credential harvesting
Emails may link to a fake login page hosted on a lookalike domain. The page mimics your real login portal and tricks users into entering their credentials. - Business email compromise (BEC)
Fraudsters impersonate executives or vendors using similar domains to initiate fake wire transfers or sensitive data requests. - Malware Distribution
Lookalike domains are also used to host malicious attachments or downloads, disguised as trusted sources.
These tactics rely on visual similarity, urgency, and user trust, which makes them especially effective in phishing campaigns. Proactive domain monitoring and strong email authentication (like DMARC enforcement) are essential to stop these attacks before they reach your inbox.
How does DMARC help with stopping lookalike domains?
DMARC, on its own, does not stop emails sent from lookalike domains because those domains are entirely separate from your legitimate ones. For example, an attacker could register ceo@yourcornpany.com (with a “rn” instead of an “m”) and send phishing emails from it, even if your real domain has perfect DMARC enforcement.
However, DMARC can help protect against lookalike domain abuse when combined with the right tools and ownership strategies. Here’s how:
- Recover the lookalike domain.
You can file a domain takedown request (often through a lawyer or outsourced domain takedown service) to reclaim the fraudulent domain. If successful, you gain control of the lookalike. - Apply DMARC enforcement with Valimail.
Once you own the domain, Valimail Enforce allows you to:- Publish strict DMARC policies for the lookalike domain
- Monitor any attempts to send mail from it
- Ensure unauthorized emails from that domain are rejected outright
- Prevent future abuse.
With DMARC enforcement in place, even on the lookalike, you effectively shut down that attack vector. Any future phishing attempts using the domain will fail DMARC and can be blocked by receiving mail servers.
So while DMARC can’t stop someone else from registering a similar-looking domain, it becomes a powerful tool once you control that domain, letting you monitor, enforce, and prevent abuse using Valimail’s platform.
What is typosquatting?
Typosquatting definition
Typosquatting is a type of cyberattack in which malicious actors register domain names that are intentionally misspelled versions of legitimate websites. These domains are designed to exploit common typing errors or visual similarities. For example, using gooogle.com instead of google.com or yourcornpany.com instead of yourcompany.com.
Once registered, these typosquatting domains can be used for:
- Phishing attacks that trick users into entering login credentials
- Malware distribution through fake downloads
- Brand impersonation to damage reputation or mislead customers
- Harvesting traffic from accidental visits
Typosquatting is especially dangerous because the domains often look almost identical to the real ones, making them hard to detect at a glance, particularly on mobile devices or in email previews.
- To protect against typosquatting, organizations often:
- Monitor for similar domain registrations
- Register high-risk variants of their domain
- Use DMARC enforcement and domain monitoring solutions like Valimail Monitor to block or track abuse
What is an example of an IDN homograph attack?
An IDN homograph attack is a lookalike domain trick in which attackers use Unicode characters from non-English alphabets that resemble standard Latin letters to create fake domains. These domains look identical to real ones in a browser but are entirely different under the hood.
For example, let’s say your legitimate domain is:
login-example.com
An attacker might register:
login-example.com
While it looks the same, this fake version uses:
“ⅼ” (lowercase L from Unicode) instead of a standard “l”
“і” (Cyrillic i) instead of a standard “i”
In the email header, most users wouldn’t notice the difference, but they’d be opening an email from a malicious sender.
To defend against an IDN homograph attack, you can:
- Use modern browsers that warn or block suspicious IDNs
- Deploy DMARC, SPF, and DKIM to stop email impersonation
- Monitor the web for registered domains that resemble your brand, including IDN variants
- Use tools like Valimail’s Lookalike Domain Finder to help detect these threats before they’re used in phishing campaigns
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.