- Guide
What Helps Protect from Phishing
Spear phishing is a category of phishing attack that strategically targets specific victims. Unlike conventional phishing, which often infects whoever it can via spam and other quantitative approaches, spear phishing opts for a qualitative approach, focusing on high-value targets with access to sensitive systems. More elaborate social engineering and advanced malware make spear phishing difficult to combat.
By offering actionable best practices for hardening your organization, this article will guide you through the ins and outs of defending against spear phishing. Although the principles we outline below should be useful for anyone who wants to combat spear phishing, we’ll lean on tools compatible with Office 365 (O365).
Executive Summary
Before we begin, let’s overview the broad genres of protection mechanisms we’ll touch on in this article.
| Protection Mechanism | Description |
|---|---|
| Email Security | Prevent fraud and unauthorized access (e.g., the DMARC protocol or end-to-end encryption) |
| Vendor Integrations | Services like Valimail Authenticate and Microsoft ATP that work with your mail software to make it more secure |
| Browser Extensions | Detect phishing domains in the browser with extensions for Chrome, such as Phishdetector and MetaCert’s Cryptonite |
| Password Managers | Easily generate and manage strong, unique passwords, either in the cloud or on-premises |
Defending Against Spear Phishing
To more concretely illustrate the tactics used by fraudsters as well as the mitigations available to savvy IT teams to mitigate these attacks, let’s look at a simple example of a spear phishing email.
Below is a raw email we’ve crafted to simulate how a primitive spear phishing attack might work. The sample needs to be primitive because we want it to demonstrate various tricks that show the need for both commonplace and more advanced protections.
Let’s take a look:
Date: Mon, 18 Apr 2022 21:36:08 -0600
Subject: Big news for Burkina Faso!
From: "Tom Sankara" <tom@burkina.gov.bf>
To: "Henri-Paul Damiba" <paul@burkina.gov.bf>
Content-Type: multipart/mixed; boundary="000000000000d7762c05dcf99350"
--000000000000d7762c05dcf99350
Hey Paul, congrats on winning the election. Hey, I think you actually got additional votes that weren’t counted.
Check out the PDF I attached to see how the stats don’t match…
Our friend Ernesto G. was saying you should message him back about this, he’s waiting for your reply: http://bvrkina.gov.bf/msg/che
--000000000000d7762c05dcf99350
Content-Type: application/octet-stream; name="vote.pdf.exe"
Content-Disposition: attachment; filename="vote.pdf.exe"
Content-Transfer-Encoding: base64
X-Attachment-Id: f_l25lg11j0
Content-ID: <f_l25lg11j0>
--000000000000d7762c05dcf99350--If you’re an experienced email administrator, some things about the message above might immediately jump out to you as distinctly phishy. Or maybe nothing seems off at all. We’ll use this email as a reference point for this section of the article, taking it apart to look at each element of the attack and how to build a defense against it.
Email Security Protocols
Notice that the sample email above doesn’t have any DKIM headers? DKIM is a method for authentication that, along with SPF, can be used by DMARC to mitigate certain types of fraudulent mail. The phishing email above pretends to be from someone on the same domain as the recipient to gain trust. You can use DMARC with DKIM and SPF to make such fraud much harder.
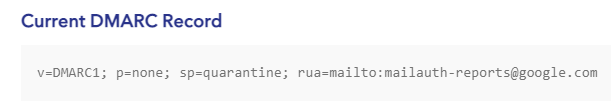
A DMARC record, using Google’s record as an example. (source)
Note that just publishing a DMARC record isn’t enough. You must also do DMARC validation on inbound mail and honor your own p=reject policy in order to stop spear phishing when using DMARC. Check out our article on using DMARC with Office 365 to learn more about deploying these protocols.
In addition, services like Valimail bolster DMARC for Office 365 users by providing robust monitoring and easy monitoring enforcement of DMARC policies.

IT teams concerned about preventing email abuse should invest in a robust DMARC setup. However, considering the sophisticated nature of spear phishing campaigns, using basic email security protocols like SPF, DKIM, and DMARC should be the first step toward a more comprehensive security strategy.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
Vendor-Specific Security Integrations
Mail providers often offer systems for protecting enterprise users from spear phishing threats. Microsoft, for example, features Windows Defender for Office 365. There’s a good chance the malware attached to our sample email would have been detected and flagged as potentially malicious by Windows Defender for Office 365’s scanners.
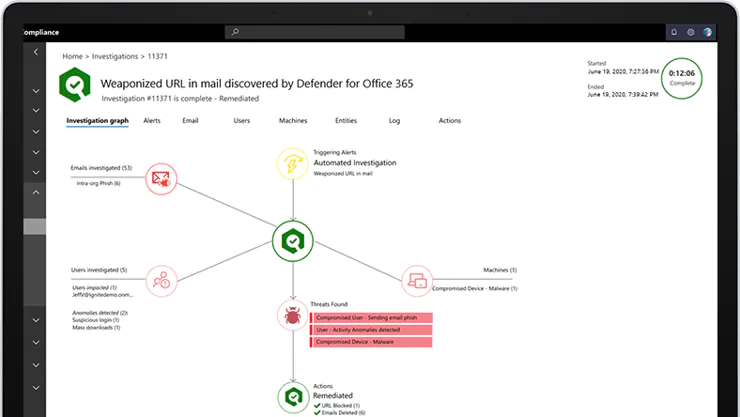
Defender for O365 goes way beyond mere static scanning of attachments for malware signatures. The Safe Attachments feature creates a virtual environment to open the attachment and observe its behavior for suspicious activity.
Browser Extensions
How do you know if the website you’re visiting is a phishing site? You can check the URL, but maybe the URL is a lookalike that’s so close to the correct domain that you won’t notice the difference?
In our sample phishing email, the correspondents are using the domain burkina.gov.bf. But did you notice that the phishing link uses bvrkina.gov.bf, with the letter “v”? Attackers could even go a step further, using Unicode to mix up obscure characters that look identical to characters in the Latin alphabet. It’s difficult to detect such a trick without extra help.
Browser extensions like MetaCert’s Cryptonite for Chrome detect and alert you when browsing a possible phishing site.
Cryptonite is far from the only player in this space. Other popular, well-known anti-phishing extensions include PhishDetector and Netcraft. Each anti-phishing extension has its own merits and should be evaluated individually according to the specific threat model of your organization.
For example, PhishDetector specializes in detecting phishing attempts related to online banking. Netcraft offers the most cross-platform support, including integration with Outlook and Gmail and extensions for Firefox, Opera, Edge, and Chrome.
Members of your organization should not be expected to deploy these extensions themselves. Instead, deployment should be initiated and enforced company-wide via the Google Admin console for managing Chrome, according to the instructions found in the Google support document Force install apps and extensions.
Layered Security
Most of the mitigations we’ve outlined so far focus on preventing successful attacks, but let’s say a scammer successfully breaches your security. What can you do to mitigate the impact of a spear phishing attack?
End-to-end encryption (E2EE) is a powerful tool for protecting the privacy of your communications. With E2EE, even if an attacker breaks into your email account, they won’t be able to access the actual data held in your inbox because you’ve encrypted with keys that are only accessible on your device.
The two preeminent E2EE mechanisms for protecting email are S/MIME and PGP. Both are effective solutions, but they have essential technical differences that admins must understand before choosing. The Information Security StackExchange thread How does PGP differ from S/MIME? is a good primer for learning how the two differ.
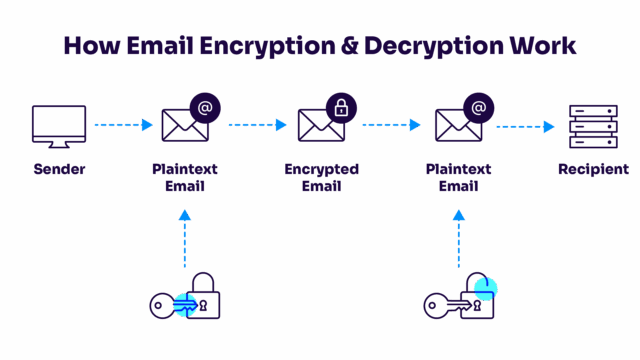
In E2EE, messages are stored encrypted. You control the keys to unlock them.
Although PGP and S/MIME are great for encrypting mail, they’re too advanced for non-technical users to contend with. Therefore, you’ll usually want to coordinate with your security team to help IT roll it out seamlessly. Solutions like Mailvelope and Flowcrypt make integrating PGP a breeze. S/MIME also enjoys a diverse market of solutions that you can integrate into your mail client, like S/MIME in Outlook Web App and many others.
Find a solution that fits your tech stack and roll it out domain wide to avoid the painful process of trying to teach cryptography to everyone in your organization.
Password managers are another fantastic tool for limiting the damage of a breach. The sample phishing email shown before includes a phishing link. What if the victim clicked the link and entered their credentials on a phishing site? The attacker would steal the username and password for the website they’re imitating and hack the victim’s account, but they usually don’t stop there.
Most people reuse passwords across multiple accounts on various websites, so the attacker would likely try the same credentials on several websites to hack as many of the victim’s accounts as possible. This practice is known as “credential stuffing” in the infosec community.
The solution is to use a strong, unique password for each account. Remembering so many passwords would require nigh-impossible mental gymnastics, so instead of relying on memory, you use a password manager.
IT admins should enforce password managers’ use as an organization-wide policy. No one should be relying on memory or other primitive methods of manual password management.
Next Steps
The suggested mitigations above are a great starting point for admins concerned about defending high-value targets from scammers. However, this small guide barely scratches the surface of the deep world of defending against spear phishing.
Where can you go from here? Finding real weaknesses using simulated phishing frameworks like Gophish is a great next step if you’ve already implemented the recommendations above. If your organization doesn’t have a security team to help run the simulated phishing campaign, hiring an external auditing firm to help will also provide immense value.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
Conclusion
With the rise of highly profitable ransomware gangs and state-sponsored threat actors, spear phishing has risen to the top in terms of threats faced by companies. According to Symantec’s Internet Security Threat Report, “spear phishing emails remained the most popular avenue for attack and were used by 65 percent of all known groups.” Spear phishing is a common way for attackers to get their foot in the virtual door. It’s a reliable attack because combating it is such a big challenge.
Fighting against spear phishing raises dozens of complex issues for security teams, all of which admins must address competently to provide a comprehensive defense. We’ve looked at diverse strategies: from scanning attachments and running attached content in a virtual environment to deploying browser extensions across your organizations that detect and alert users when they are on a possible phishing page. Other attacks outside this article’s scope include voice phishing (vishing) and SMS-based scams (smishing). This article was a high-level introduction to a topic that can go infinitely deeper.
With hard work and the diligent application of the techniques outlined in this article, you can lessen the risk posed by spear phishing to you and your team members.
Explore the chapters:
- 1. Introduction – Email Security Best Practices
- 2. MTA-STS
- 3. DKIM Selector
- 4. DMARC vs DKIM
- 5. DMARC Office 365
- 6. SPF Failure
- 7. SPF Softfail vs Hardfail
- 8. What Helps Protect from Phishing
- 9. Fixing the Error “No DMARC Record Found”
- 10. DKIM Office 365
- 11. How to Configure DMARC Policy to Reject or Quarantine
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.