- Guide
Executive Phishing: Real World Examples & Strategies
Executive phishing, also known as CEO fraud, is a form of attack in which scammers impersonate a high-level executive to trick employees or customers. Unlike whaling, where attackers set their sights on hacking influential targets like executives, executive phishing targets non-executives by using the reputation and authority of a trusted executive.
Executive phishing is especially dangerous when combined with Business Email Compromise (BEC). BEC allows attackers to send phishing emails using the actual email address of an influential executive.
Although executive phishing is often sophisticated, good defenses can protect your organization and reduce risk. This article will examine how executive phishing attacks work in the real world and strategies for mitigating your organization’s risk.
What Is Executive Phishing?
Executive phishing is where cybercriminals impersonate the CEO or another high-ranking executive of an organization to deceive employees. They typically target employees in finance or HR to execute unauthorized transactions or reveal sensitive data or information.
However, anyone can be a target. Once a cybercriminal gets access to your systems, there’s no stopping the extent of the damage.
How Does Executive Phishing (or CEO Fraud) Work?
While not every executive phishing attack will look the same, here’s the basic process of how it works:
- Target Selection: Attackers choose an executive or senior official within an organization to impersonate. This could be the CEO, CFO, or another high-ranking individual.
- Email Compromise or Spoofing: Attackers either compromise the executive’s email account or create a spoofed email address that closely resembles the executive’s actual email. The goal is to make the email appear as if it’s genuinely coming from the executive.
- Crafting the Message: The attacker, posing as the executive, crafts a message targeting an employee, often someone in finance or HR. The message might request an urgent wire transfer, ask for sensitive employee data (like W-2 forms), or request other confidential information.
- Sense of Urgency: Similar to other phishing attacks, these emails often convey a sense of urgency. The “executive” might say they need the information or funds for a confidential deal or time-sensitive opportunity.
- Payload Delivery: If the targeted employee believes the email is genuine, they might process the wire transfer, send out confidential data, or provide access to restricted systems.
- Exploitation: Once the attackers have the funds or information, they can disappear, often making it challenging to trace or recover the stolen assets.
Spotting an Executive Phishing Attack
Sophisticated phishing attacks are much harder to detect than old-fashioned spammy junk mail about Nigerian princes. Scammers put more effort into these attacks to avoid detection. When combined with clone phishing and BEC, executive phishing can be so difficult to detect that only an additional verification outside of email itself suffices in thwarting this technique.Here are some common indicators of an executive phishing attack.
Here are some common indicators of an executive phishing attack.
Signs that point to an executive phishing attack
| Indicator | Description |
|---|---|
| External sender domain | Mail from an origin claiming to be the executive’s “personal” account |
| Abnormal messaging channels | Message from informal, insecure channel instead of standard, secure channel |
| Claims of lost account access | Claims to be locked out of a resource they’d normally have access to |
| Unusual style or tone | Messaging differs from style or tone of communication typical to that executive |
| Bulk emails with attachments or links | Sent en masse asking employees or customers to click a link or download a file. |
The above signs are huge red flags. Unfortunately, an attacker willing to go through the work required to execute an executive phishing attack will also be aware of these issues and do their best to avoid detection. Let’s look at a realistic attack scenario to see just how sneaky these executive phishing attacks can get.
Understanding Executive Phishing Attacks
Executive phishing exploits the trust and authority of a high-profile figure. By impersonating someone important, attackers can leverage that power and trust to invoke urgency and trick recipients into making foolish decisions.
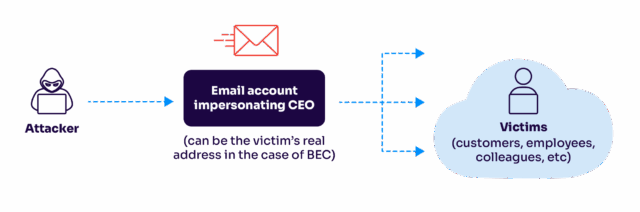
An overview of an executive phishing attack.
The most well-known executive phishing attack occurred in 2016 against Snapchat. Scammers impersonated the CEO and convinced an HR staffer to send them sensitive financial data belonging to the company. This attack woke the world up to the threat of executive phishing, though it was hardly the first time it happened.
Since then, executive phishing attacks have become more prominent and sophisticated. Attackers have even taken executive phishing beyond email by combining it with other phishing techniques like voice calls (vishing), text message-based phishing (smishing), and social media phishing.
Recreating an Executive Phishing Attack
Now that we’ve covered the concept let’s review what this executive phishing looks like in practice.
Imagine you help with payroll as a human resources manager for a small to medium-sized business that sells paper accessories. Most employees aren’t tech savvy. You only need to know enough to operate a simple point-and-click payroll application.
You receive a message from your boss on WhatsApp:
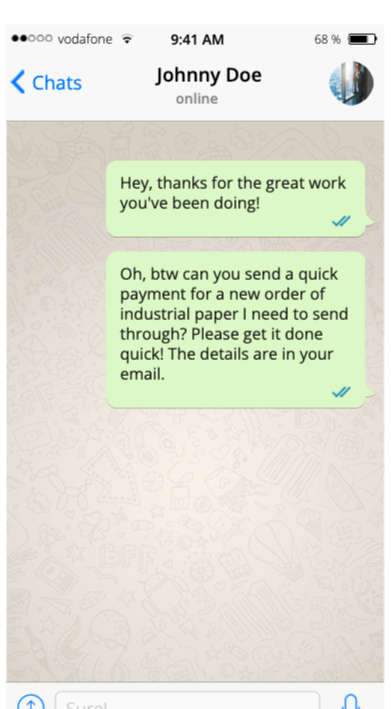
You don’t know this, but it isn’t actually your boss. The phone number is correct, but an attacker has SIM-swapped your boss’s phone number to hijack their WhatsApp account. However, you have no idea, so you check your email.
Sure enough, you have an email from your boss:
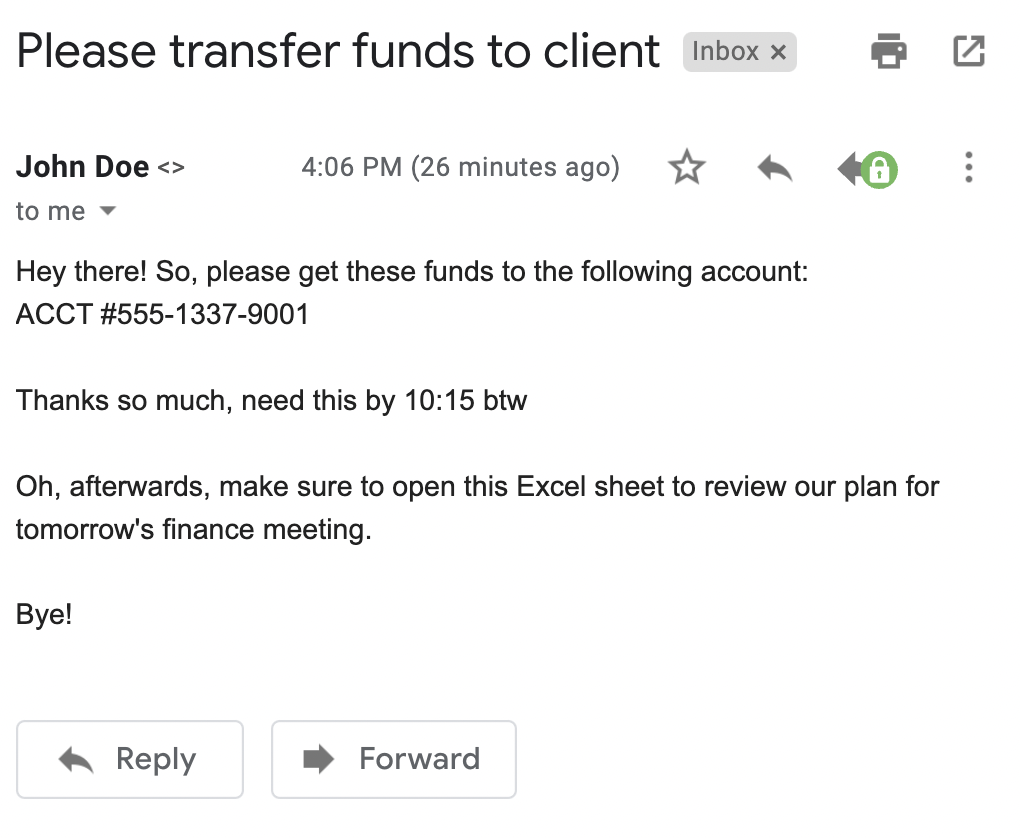
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
It seems easy enough, so you go ahead and transfer the funds. You don’t know that you’ve just sent ten thousand dollars to scammers who have been studying the business you work at for months. As part of their reconnaissance, they noticed that SPF, DKIM, or DMARC don’t protect your company’s domain name.
The lack of SPF, DKIM, and DMARC allows the attacker to impersonate your boss’s email address. After sending the funds, you follow the remaining instructions and open the attached Excel spreadsheet. When you open it, a message indicates the spreadsheet needs permission to run macros. Of course, you click it.
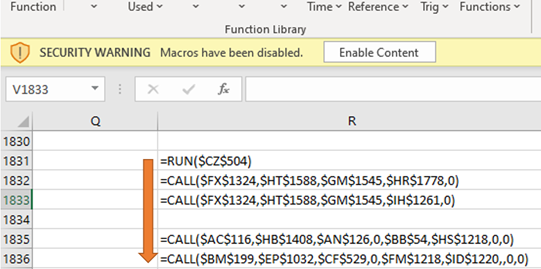
That’s when you realize something is wrong. After a few minutes, your computer shuts down. You walk out into the hallway and find total pandemonium – every computer in the building is shut down.
Then a message pops onto every screen at the same time.
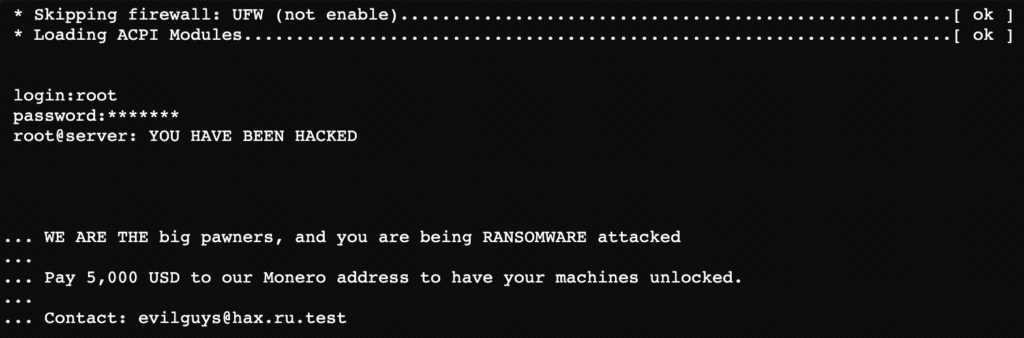
You feel sick to your stomach. Everyone is dead silent. If only you could have noticed. But how could you have done anything? After all, you’re an HR professional, not a cybersecurity wizard. Why didn’t the IT team prevent this?
Defense and Mitigations for Executive Phishing Attacks
Old email phishing scams from the late 90s and early 2000s were easy to detect. Most victims were elderly or didn’t understand the Internet well enough to realize they were being victimized.
Today, most users are familiar with these scams. That’s why attackers have developed more sophisticated attacks like executive phishing. However, you can significantly reduce the risk of executive phishing in your organization by understanding the indicators of executive phishing, protecting your digital identity, and implementing strong security controls.
Below are specific best practices you can follow to mitigate executive phishing.
Flag External Emails with Warnings
Often, an attacker will send a phishing email from a domain name that looks like your organization’s. For example, they may replace the letter “o” with a number “0” or replace the letter “a” with the Greek alpha “α”. Unless you’re familiar with these homograph attacks and carefully verify the legitimacy of every email’s domain, this attack is likely to work. If not against you, then at least against someone in your organization.
Fortunately, most popular email applications provide a mechanism for warning you when an email comes from outside of your organization. Below are links to instructions for enabling external sender warnings using several of popular email applications:

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
- Control Gmail external recipient warnings
- Configure warning for External Senders on Office 365
- External Email Alert addon for Thunderbird
In addition to these warnings, organizations should implement a company-wide policy that restricts external sharing of sensitive data. More sensitive data should come with additional verification steps, like calling the person or organizing a meeting to confirm important actions. The Traffic Light Protocol developed by the Cybersecurity & Infrastructure Security Agency (CISA) is a popular standard for handling sensitive information.
Protect Your Digital Identity
Securing and verifying digital identity is a deep rabbit hole, and there’s always more you can do. However, we can start you out with some basics that give you an idea of the technology available.
For example, in the example attack we used earlier in the article, the attacker smished the target by SIM swapping the CEO’s phone number. This gave him access to the CEO’s WhatsApp account and thus made his messages indistinguishable from the genuine article.
Most carriers allow you to lock down your SIM with a numerical PIN, making it harder for social engineers to pilfer. The AARP has a more in-depth guide to protecting yourself from SIM swapping: How to Protect Yourself and Your Mobile Phone From SIM Swap Scams.
How did the attacker figure out the identity and contact information of the human resources manager to begin with? Organizations should implement procedures to avoid making contact information available on sites like LinkedIn, Facebook, and so on. Many of these sites also have features to avoid making your org chart immediately apparent.
Cryptographic technologies like PGP and S/MIME can also help confirm identity. However, this is too burdensome for most nontechnical workers to manage conveniently. You’ll want to use an easy-to-manage end-to-end encryption solution like FlowCrypt or Thunderbird’s PGP addon to make things easier. Encryption goes beyond just email, though. Chat and even voice calls can be protected using strong end-to-end encryption.
Password managers, phishing awareness training, we could go on. The best way to begin is to consult with a cybersecurity expert that specializes in identity management and can set up a diverse defense for your digital identity.
Implement Robust Email Security
In the previous section, we detailed a realistic attack that took advantage of email fraud. If SPF, DKIM, and DMARC don’t protect your domain, you’re making it much easier for attackers to impersonate people within your company. This puts your employees at risk and makes it easier for hackers to send out spam from your domain, trashing your domain’s reputation.
The good news is that DMARC is easier than ever to deploy. Services like Valimail Enforce allow even non-technical people to set up a strong email security policy on Office 365. Other platforms also have great resources, like Gmail’s Advanced Protection Program.
Note that simply publishing a DMARC policy isn’t enough to protect your own company’s inboxes. You must also do DMARC validation on inbound mail and honor published policies to keep forged mail out of your employee’s inboxes. To learn more about the intricacies of email security best practices, check out The Guide To Email Security Best Practices With Examples.

Educate employees by sharing this guide with them

Implement email filtering tools including inbound DMARC validation

Publish a DMARC record for your domain
Conclusion
Executive phishing is an advanced attack in which scammers impersonate the CEO of a company to exploit the power dynamic of that position. Typically, the attack targets employees and customers. Worse yet, advanced persistent threats have taken this attack to the next level by combining it with other sophisticated techniques like smishing, vishing, and social media phishing.
However, strong defenses exist that you can take advantage of to stay safe. You can keep yourself safe by adding warnings for emails from external domains, managing identity using cryptography, and applying other tactics discussed in this article.
Explore the chapters:
- 1. Introduction - Complete Guide to Phishing
- 2. Spear Phishing vs. Phishing
- 3. Clone Phishing: How it Works and Defenses
- 4. What Is a Common Indicator of a Phishing Attempt?
- 5. Executive Phishing
- 6. URL Phishing: Real World Examples & Strategies
- 7. Phishing Prevention Best Practices
- 8. Phishing vs. Pharming
- 9. Payment Confirmation Spam Emails
- 10. Phishing vs. Spoofing
- 11. Domain Hijacking
- 12. What does BEC stand for
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.